Microsoft AD FS SAML SSO
In this section, we will show you how to set up your own custom SAML application for Microsoft AD FS.
In AD FS, a relying party (RP) trust needs to be set up. You can supply our SP metadata file, usually located at https://<your-hosted-url>/.well-known/sp-metadata and let AD FS automatically pick up the configuration.
If you are manually entering the details then you'll find the details you need in this section. The public certificate is needed for Signature verification and is usually located at https://<your-hosted-url>/.well-known/saml.cer for Signature verification.
You will also need to map some attributes of the claims so we can fetch the profile information for your user.
Create a claims aware Relying Party Trust using federation metadata
- In Server Manager, click Tools, and then select AD FS Management.
- Under Actions, click Add Relying Party Trust.
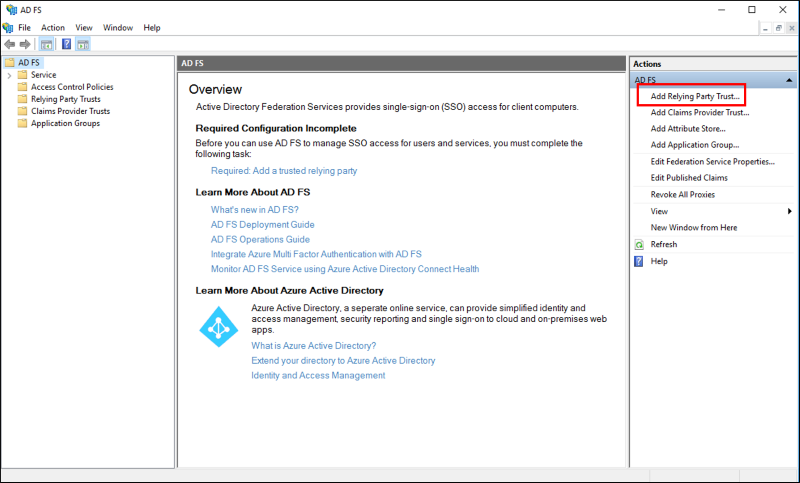
- On the Welcome page, choose Claims aware and click Start.
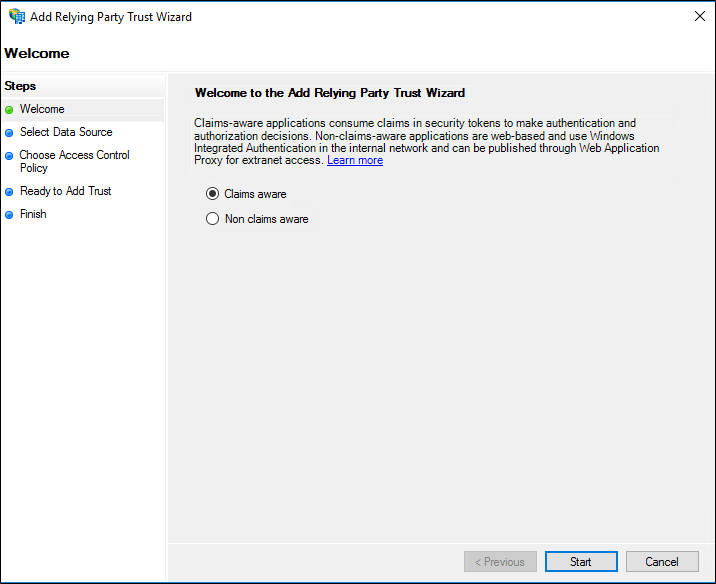
- On the Select Data Source page, click Import data about the relying party published online or on a local network. In Federation metadata address (host name or URL), type the federation metadata URL or host name for the partner, and then click Next.
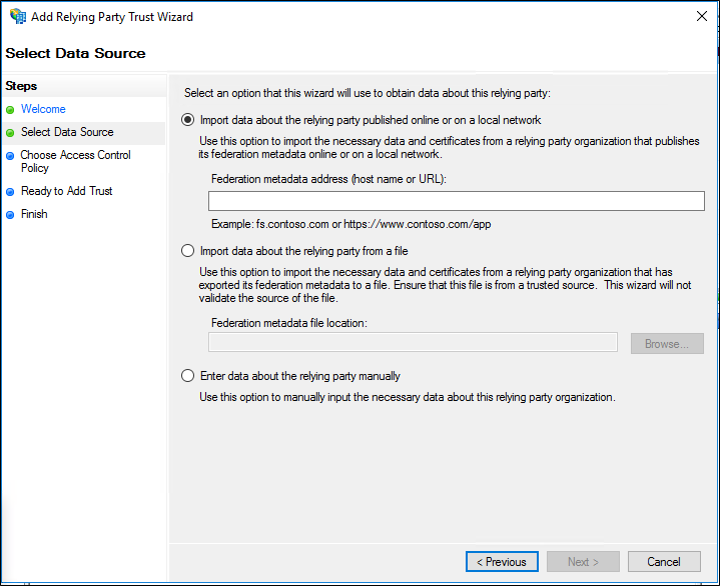
- On the Specify Display Name page type a name in Display name, under Notes type a description for this relying party trust, and then click Next.
- On the Choose Issuance Authorization Rules page, select either Permit all users to access this relying party or Deny all users access to this relying party, and then click Next.
- On the Ready to Add Trust page, review the settings, and then click Next to save your relying party trust information.
- On the Finish page, click Close. This action automatically displays the Edit Claim Rules dialog box.
- Mapping attributes: On the Configure Claim Rule screen, enter a Claim Rule Name of your choice, select Active Directory as the Attribute Store, then add the following mapping:
- From the LDAP Attribute column, select
E-Mail-Addresses. From the Outgoing Claim Type, typeE-Mail Address. - From the LDAP Attribute column, select
Given-Name. From the Outgoing Claim Type, typeGiven Name. - From the LDAP Attribute column, select
Surname. From the Outgoing Claim Type, typeSurname. - From the LDAP Attribute column, select
User-Principal-Name. From the Outgoing Claim Type, typeName ID.
- Transform Rule: Create a transform rule mapping the incoming
Email-Addressto outgoingNameID(of typeEmail), ADFS by default sendsNameIDasUnspecifiedwhich results in anInvalidNameIDPolicyerror if this step is missed.
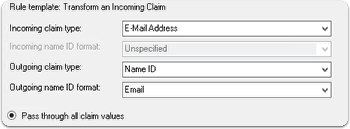
If you'd rather use Claim rule language then the following rule can be applied:
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"] => issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress");
- Finally open Windows PowerShell as an administrator, then run the following command:
Set-ADFSRelyingPartyTrust -TargetName <display-name> -SamlResponseSignature "MessageAndAssertion"